In an extraordinary blend of cybersecurity, performance, and political statement, a pseudonymous hacker known as Martha Root remotely destroyed three white supremacist-linked websites live during a major tech conference in Hamburg, Germany in early January 2026. (TechCrunch)
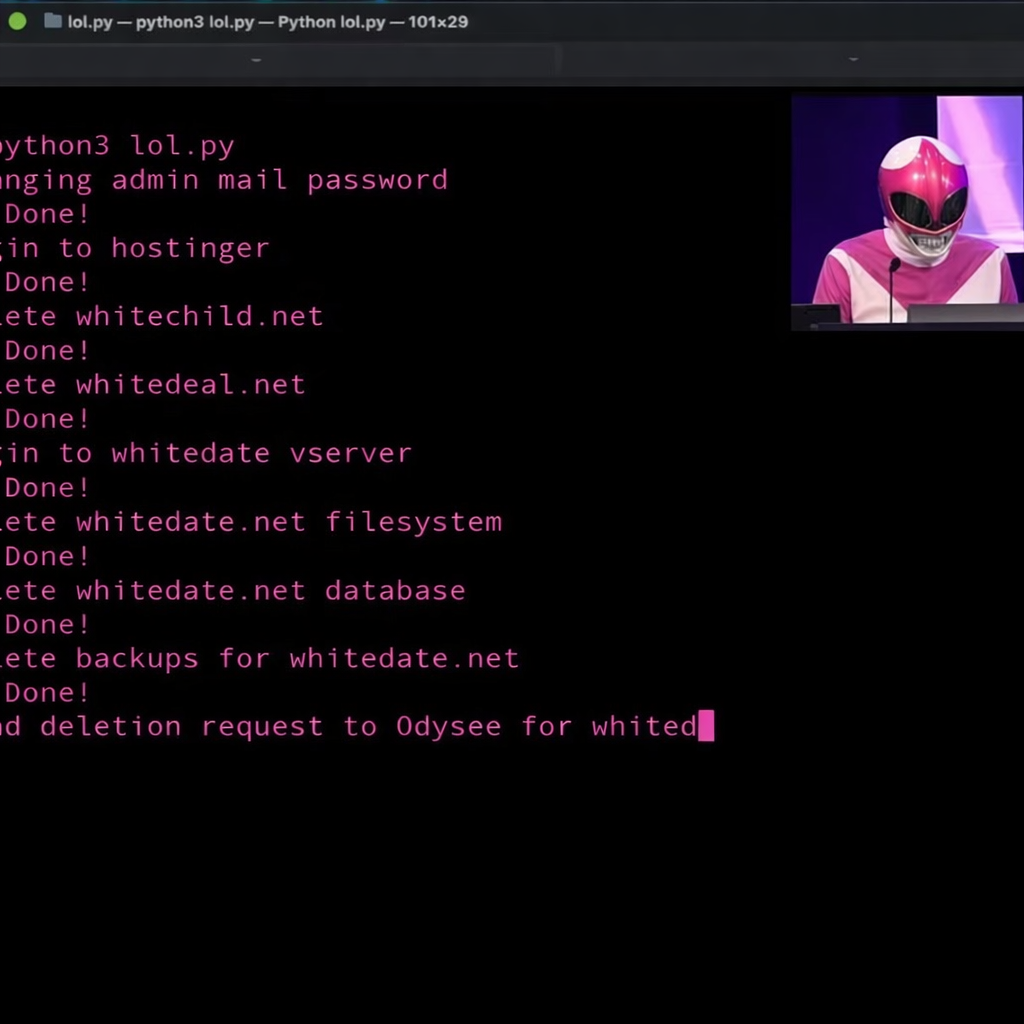
The incident unfolded at the 39th Chaos Communication Congress (39C3) — one of Europe’s largest annual gatherings of hackers, security researchers, and digital rights advocates. As hundreds of attendees watched, Root took to the stage dressed in a Pink Power Ranger costume to deliver what organizers described as a demonstration of extremist infrastructure vulnerabilities and the power of ethical hacking. (TechCrunch)
Targets: WhiteDate, WhiteChild & WhiteDeal
The three sites targeted — WhiteDate, WhiteChild, and WhiteDeal — were online platforms catering to white supremacist ideologies and communities. WhiteDate was widely described in media as a “Tinder for Nazis,” designed to match users with similar racist beliefs. WhiteChild claimed to facilitate connections between white supremacist sperm and egg donors, and WhiteDeal operated as a labor marketplace exclusively for people aligned with far-right views. (Yahoo News)
In a succinct live demonstration, Root executed scripted commands that fully deleted the servers, backups, and related infrastructure underpinning all three sites. Spectators reportedly applauded as each platform disappeared from the internet in real time. (Cybernews)
Infiltration and Data Exposure
Before the dramatic takedown, Root reportedly gained access to these platforms by exploiting their lax security. According to Root’s own account and conference materials, she deployed AI-driven chatbot accounts that successfully passed the sites’ verification processes and interacted with real users. This allowed her to harvest a significant volume of public data, including names, photos, descriptions, and precise geolocation metadata embedded in profile images. (Cybernews)
Root later made portions of this data public as part of a dataset dubbed “WhiteLeaks.” Investigative collaborators such as the nonprofit DDoSecrets have since made the wider dataset — reported to be roughly 100 GB — available to vetted journalists and researchers for further scrutiny. (archive.vn)
Describing the security of these platforms, Root quipped that it showed “poor cybersecurity hygiene that would make even your grandma’s AOL account blush,” a pointed critique of how extremist sites often prioritize ideology over technical safeguards. (Yahoo News)
Reactions and Debate
The administrator of the three sites confirmed on social media that the hacking occurred, denouncing it as “cyberterrorism” and vowing legal or other repercussions. Critics and supporters alike have since taken to social platforms to argue about the ethics and legality of Root’s actions. (Yahoo News)
Meanwhile, many in the cybersecurity community framed the event as a striking demonstration of how easily insecure digital infrastructure can be dismantled, particularly when it is used to foster harmful or extremist agendas. (The Daily Dot)
Looking Forward
While the long-term impact of the takedown remains to be seen, the event has reignited conversations about the responsibilities of platform operators, the potential for hacktivism to disrupt extremist networks, and the boundaries between activism and unlawful interference — especially in a live, public forum. (futurism.com)
C. Stewart
If you’d like, I can also provide a timeline of how the hack unfolded or a summary of the key technical methods used in the operation.